Tisco: Official Distributor of Strike in the United States. Discover security risks through world-class manual penetration testing with Strike.
Beyond traditional penetration testing:
Discover Strike — Professional Penetration Testing Services by Tisco Networks
Through advanced penetration testing and ethical hacking, Strike helps businesses identify vulnerabilities before cybercriminals exploit them. Our cybersecurity experts simulate real-world attacks to assess your systems, applications, and networks — providing actionable insights to improve your security posture.
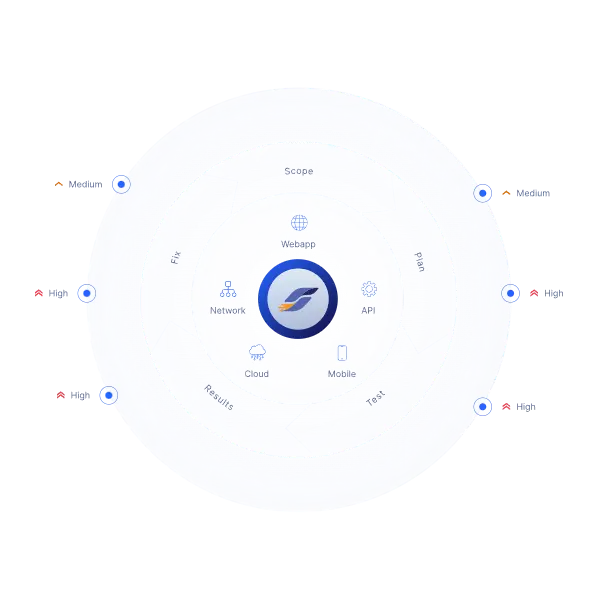
This combination of high-quality human services with a modern technology platform redefines the traditional concept of penetration testing. While everything falls under this practice, our clients can access a comprehensive portfolio of solutions ranging from automated vulnerability scans to advanced Red Teaming services.
35%
What we find is critical.
4.7/5
Average rating of ethical hackers.
35%
To find the first vulnerability.
Choose the penetration testing service that best fits your business.
Premium Penetration Testing (Pay per Time)
Strike’s most advanced and comprehensive security assessment, delivered by our in-house ethical hacking team together with a Striker specialized in your technologies. An expert is assigned to your environment to run targeted penetration testing using real-world attack techniques that uncover vulnerabilities automated scanners miss. The engagement scope is fully customizable to match your specific security requirements.
Included Technologies
Web Apps, APIs, Mobile (Android & iOS), Cloud, On-Premise, AI/LLMs, Blockchain, Hardware.
Ideal for:
Organizations that require a high-impact security assessment with a personalized approach.
Collaborative Penetration Testing (Pay Only for Vulnerabilities Found)
Multiple Strikers work simultaneously with the client’s team to enhance efficiency and coverage. It includes real-time vulnerability discovery, task distribution, and continuous communication with the client.
Included Technologies
Web Apps, APIs, Cloud, On-Premise, AI/LLMs.
Ideal for:
Organizations seeking a fast, interactive, and comprehensive penetration testing approach.
Red Team Exercises
Simulates real-world attacks to assess detection and response capabilities. Includes asset identification, execution of TTPs (Tactics, Techniques, and Procedures), and strategic defense recommendations.
Included Technologies
Enterprise networks, Cloud environments, On-Premises infrastructure, Active Directory, complex enterprise environments.
Ideal for:
Organizations seeking to evaluate their defenses against targeted attacks and APTs (Advanced Persistent Threats).
Blockchain & AI Security Testing
Security assessments for blockchain applications and AI/LLM implementations. Focused on smart contract vulnerabilities, adversarial AI attacks, and integrity risks.
Included Technologies
Blockchain, Smart Contracts, AI/LLMs.
Ideal for:
Organizations that require a high-impact security assessment with a customized approach.
Onsite Pentesting*
On-site security assessments to identify physical and network risks. Includes infrastructure evaluation, internal network analysis, and physical security testing.
Included Technologies
Internal networks, physical security, On-Premises, Hardware.
Ideal for:
Companies with critical infrastructure or environments where physical security is a key factor.
Hardware Pentesting
Security analysis of physical devices such as routers, payment terminals, and embedded systems. Includes hardware/software attack simulations, firmware reverse engineering, and security recommendations.
Included Technologies
IoT, payment terminals, embedded systems, hardware.
Ideal for:
Companies that develop or implement connected devices and require security validation.
*Onsite Pentesting: Subject to availability and minimum engagement requirements.
**Hardware Pentesting: Subject to availability. Shipping costs are covered by the client.
Testing Approaches
At Strike, we adapt our penetration testing approach to your specific security needs:
Black Box (External Testing):
No credentials are provided. It simulates an external attacker and focuses on OSINT, reconnaissance, authentication bypass, server misconfigurations, endpoint enumeration, fuzzing, phishing, and network scanning.
Grey Box (Internal & External Testing):
Credentials are provided to the tester. It focuses on privilege escalation of authenticated users, horizontal and vertical access control, advanced API interactions, authorization failures, excessive data exposure, and role-based API restriction issues.
White Box (Internal Testing):
Full access to the system architecture, source code, and configurations. Enables an in-depth security assessment, including review of secure coding practices, business-logic flaws, and detection of backdoors.
Discover the most innovative pentesting platform in the market
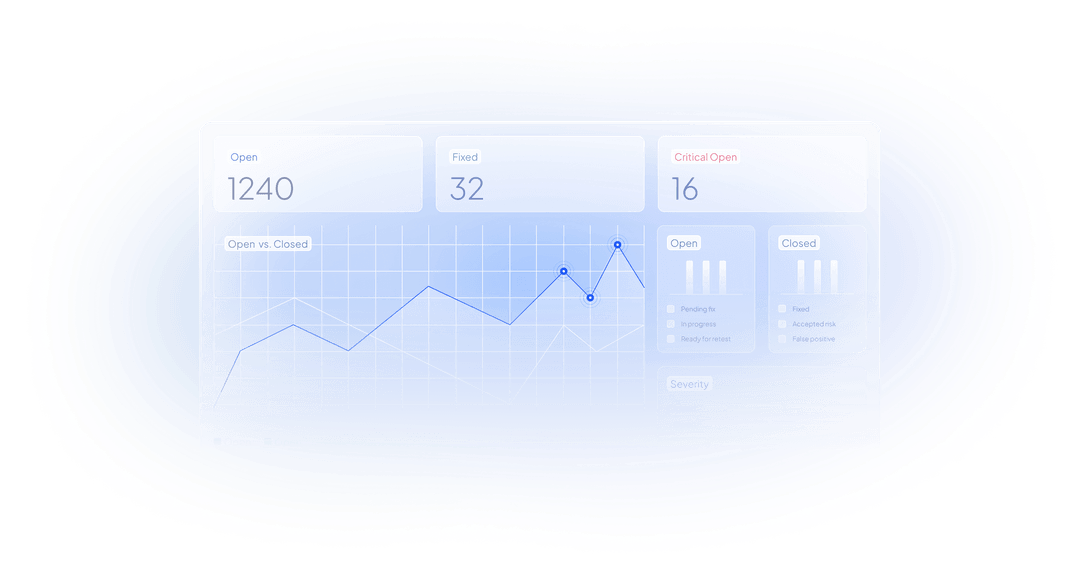

Suggested Fixes & Retesting
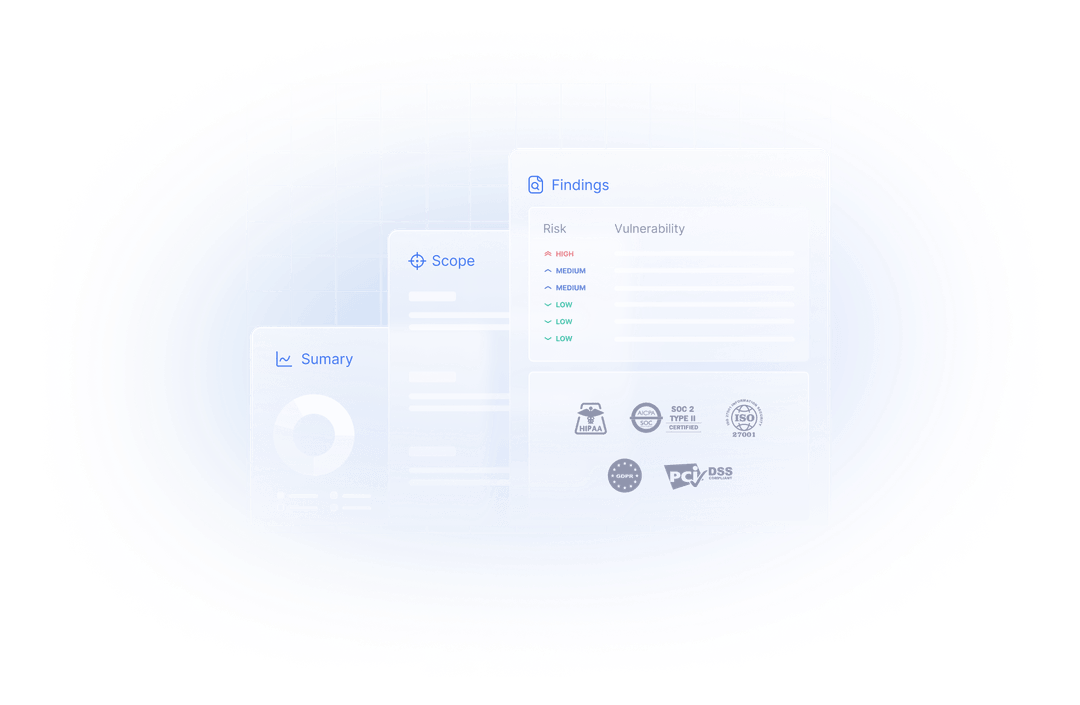
Reports

Vulnerability Manager

Integrations
Why Strike?
Our team of expert ethical hackers has years of experience in offensive security, delivering customized assessments aligned with your business needs. We provide clear, detailed reports with prioritized remediation steps, ensuring actionable recommendations to strengthen your security posture.
With a strong commitment to excellence, Strike offers personalized services that help companies proactively address cyber threats and build resilient security strategies.
Strikers
4.7/5
95%
Pentests con vulnerabilidades de alto impacto
<4%
Contact us to learn how we can help you.
It’s time to boost your business with cutting-edge methodologies and technology.
Write to us or give us a call!
2024 © TISCO NETWORKS. All rights reserved.

